Choosing an OAuth Provider
In today's interconnected digital ecosystem, implementing secure and seamless authentication and authorization mechanisms is paramount for the success of any application. In our last post, we broadly discussed OAuth 2.0, which has emerged as a widely adopted protocol for delegated authorization, enabling applications to access user resources securely. However, choosing the right OAuth 2.0 provider can be a daunting task, with various factors to consider. In this blog post, we'll explore key considerations to help you navigate the landscape and choose the OAuth 2.0 provider that best fits your application's needs.
Understanding OAuth 2.0 Providers
OAuth 2.0 providers are services that implement the OAuth 2.0 protocol, providing authentication and authorization capabilities to applications. These providers manage user authentication, issue access tokens, and enforce access control policies, allowing applications to securely access user resources on their behalf.
Key Considerations
Security and Compliance
- Security: Prioritize providers that adhere to industry best practices for security, such as encryption, secure token storage, and protection against common vulnerabilities.
- Compliance: Ensure the provider complies with relevant regulatory standards and requirements, such as GDPR, HIPAA, or PCI DSS, if applicable to your application.
Ease of Integration
- Choose a provider that offers easy integration with your application's existing infrastructure, frameworks, and programming languages. Look for comprehensive documentation, SDKs, and libraries to streamline the integration process.
- Consider providers that offer out-of-the-box support for popular platforms and frameworks, such as web applications, mobile apps, and APIs.
Scalability and Performance
- Evaluate the provider's scalability and performance capabilities to ensure that it can handle your application's current and future authentication and authorization needs.
- Look for providers that offer high availability, load balancing, and scalability features to accommodate growth and spikes in user traffic.
Developer Experience
- Assess the developer experience provided by the OAuth 2.0 provider, including ease of use, developer tools, and support resources.
- Choose providers that offer intuitive developer portals, sandbox environments, and interactive documentation to facilitate development and testing.
Customization and Control
- Evaluate the level of customization and control offered by the provider, such as configuring authentication policies, user attributes, and access control rules.
- Look for providers that allow you to tailor the authentication and authorization workflows to meet your application's specific requirements and use cases.
Cost and Pricing:
- Understand the cost structure and pricing model of the OAuth 2.0 provider, including any subscription fees, usage-based charges, or additional costs for premium features.
- Consider your budget and cost constraints when evaluating providers, and choose one that offers a pricing plan that aligns with your application's needs and scalability requirements.
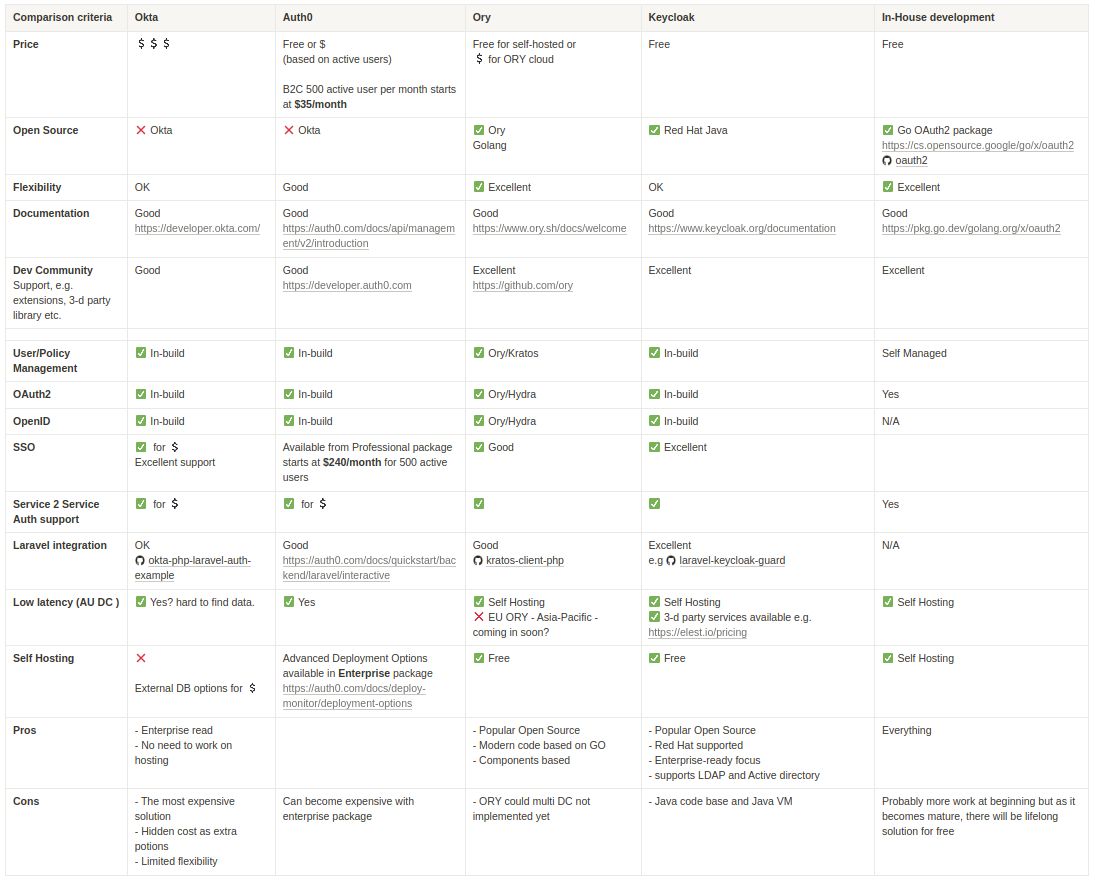
Open-source OAuth 2.0 projects vs full-fledged solutions
When choosing between open-source OAuth 2.0 projects and full-fledged solutions for your authentication and authorization needs, it's essential to consider factors such as flexibility, customization, scalability, ease of integration, maintenance overhead, and compliance requirements. Let's explore the considerations for both options:
Open-Source OAuth 2.0 Projects
-
Flexibility and Customization: Open-source OAuth 2.0 projects offer a high degree of flexibility and customization, allowing you to tailor the authentication and authorization mechanisms to fit your specific requirements and use cases.
-
Community Support: Open-source projects often benefit from active community support, with developers contributing code, providing feedback, and addressing issues. This can result in rapid development, bug fixes, and improvements over time.
-
Integration: Open-source OAuth 2.0 projects can be integrated into existing applications and frameworks, providing seamless authentication and authorization capabilities without requiring significant changes to your application architecture.
-
Control: With open-source projects, you have full control over the implementation, configuration, and deployment of the OAuth 2.0 infrastructure. This allows you to fine-tune security settings, customize user experiences, and integrate with other systems as needed.
Full-Fledged Solutions
-
Out-of-the-Box Functionality: Full-fledged solutions typically offer comprehensive features and functionality out of the box, including user management, authentication flows, authorization policies, and integration with other identity providers and systems.
-
Ease of Use: They often come with user-friendly interfaces, dashboards, and administrative tools that make it easier to configure, manage, and monitor the authentication and authorization infrastructure.
-
Scalability and Performance: These solutions are often designed to be highly scalable and performant, capable of handling large volumes of user authentication and authorization requests efficiently.
-
Compliance and Security: They may come with built-in support for compliance standards such as GDPR, HIPAA, and PCI DSS, as well as security features such as multi-factor authentication, audit logging, and threat detection.
The choice between open-source OAuth 2.0 projects and full-fledged solutions depends on your specific requirements, preferences, and constraints. Evaluate the trade-offs in terms of flexibility, ease of use, scalability, compliance, and long-term support to make an informed decision that aligns with your project goals.
Ory Hydra as Our OAuth 2.0 Provider - A Decision Journey
In our quest for an OAuth 2.0 provider that aligns seamlessly with our application's requirements and vision, we embarked on a thorough evaluation process to determine the best solution.
After careful consideration and analysis of various factors, we chose Ory Hydra as our OAuth 2.0 provider. Let's talk about main reasons which stand out from others
-
Modular and Extensible Architecture: Ory Hydra stood out for its extensibility and customization capabilities. Its modular architecture allows us to tailor the authentication and authorization workflows to our precise needs, ensuring a seamless integration with our existing infrastructure and workflows.
-
Focus on Security and Compliance: Ory Hydra places a strong emphasis on security and compliance, with built-in support for industry-standard security features such as encryption, secure token storage, and protection against common vulnerabilities. Its adherence to best practices and compliance standards gives us confidence in the security of our authentication infrastructure.
-
Scalability and Performance: Ory Hydra is designed for scalability and performance, with features such as horizontal scaling, load balancing, and optimized resource utilization. Its lightweight footprint and efficient architecture ensures that we could meet the demands of our growing user base without compromising on performance or reliability.
-
Developer Experience: Ory Hydra prioritizes a positive developer experience, offering comprehensive documentation, intuitive APIs, and developer-friendly tools. The clear and concise documentation, along with interactive tutorials and examples, make it easy for our development team to get started with Hydra and integrate it seamlessly into our applications. This focus on developer experience reduces the learning curve and accelerates the integration process, saving us time and resources.
-
Community Support and Open Source Nature: Ory Hydra's open-source nature and active community support were significant factors in our decision. The vibrant community surrounding Hydra provides valuable resources, including contributions, feedback, and support. This community-driven development model ensures ongoing improvements, updates, and bug fixes, keeping Hydra at the forefront of OAuth 2.0 providers and ensuring its longevity as a reliable solution for our authentication needs.
-
Cost-effectiveness: Ory Hydra's open-source nature and community-driven development model make it a cost-effective solution for our products. With no licensing fees or subscription costs, we could allocate resources more efficiently and invest in other areas of our business while still benefiting from a robust and feature-rich OAuth 2.0 provider.
Overall, these reasons make Ory Hydra stand out from other OAuth 2.0 providers and align closely with our application's requirements and objectives. Moreover, the fact that Ory Hydra is built using Go further strengthens its appeal for our organization. The use of this powerful programming language in building Ory Hydra aligns well with our organization's preferences and expertise in the language. It not only enhances the performance, security, and scalability of our authentication infrastructure but also simplifies maintenance and ensures compatibility across different environments. This further solidifies our decision to choose Ory Hydra as our OAuth 2.0 provider and underscores its position as a standout solution in the landscape of authentication and authorization providers.